Last updated on • Dec 19, 2016
-
- SocialTrove
-
Funded by U.S. Army Research Laboratory and NSF,
SocialTrove is a scalable and distributed summarization service for streams of
high dimensional social content.
SocialTrove provides API to hierarchically organize incoming data in a streaming fashion,
based on application provided similarity measurement,
and query it for matching objects at different granularities.
Built on top of Apache Spark, HDFS, and Memcache, the system achieves high throughput and low latency.
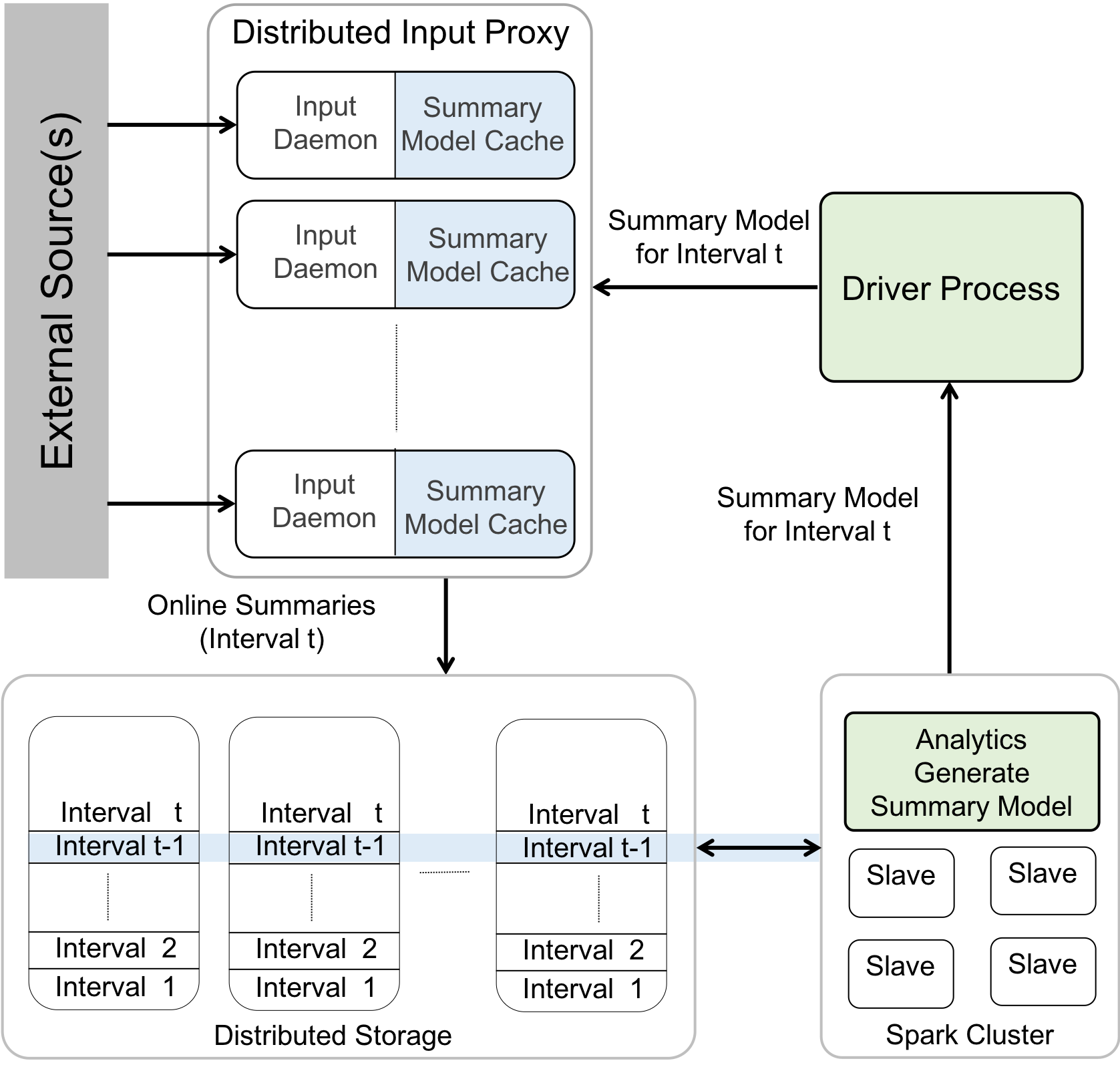

Collaborative research with Prof. Indranil Gupta (UIUC),
Mudhakar Srivatsa, and Raghu Ganti (IBM Research), resulted in a
peer-reviewed conference paper
in ICAC 2015, and received a Best Paper Award.
-
- Apollo Social Sensing Toolkit
-
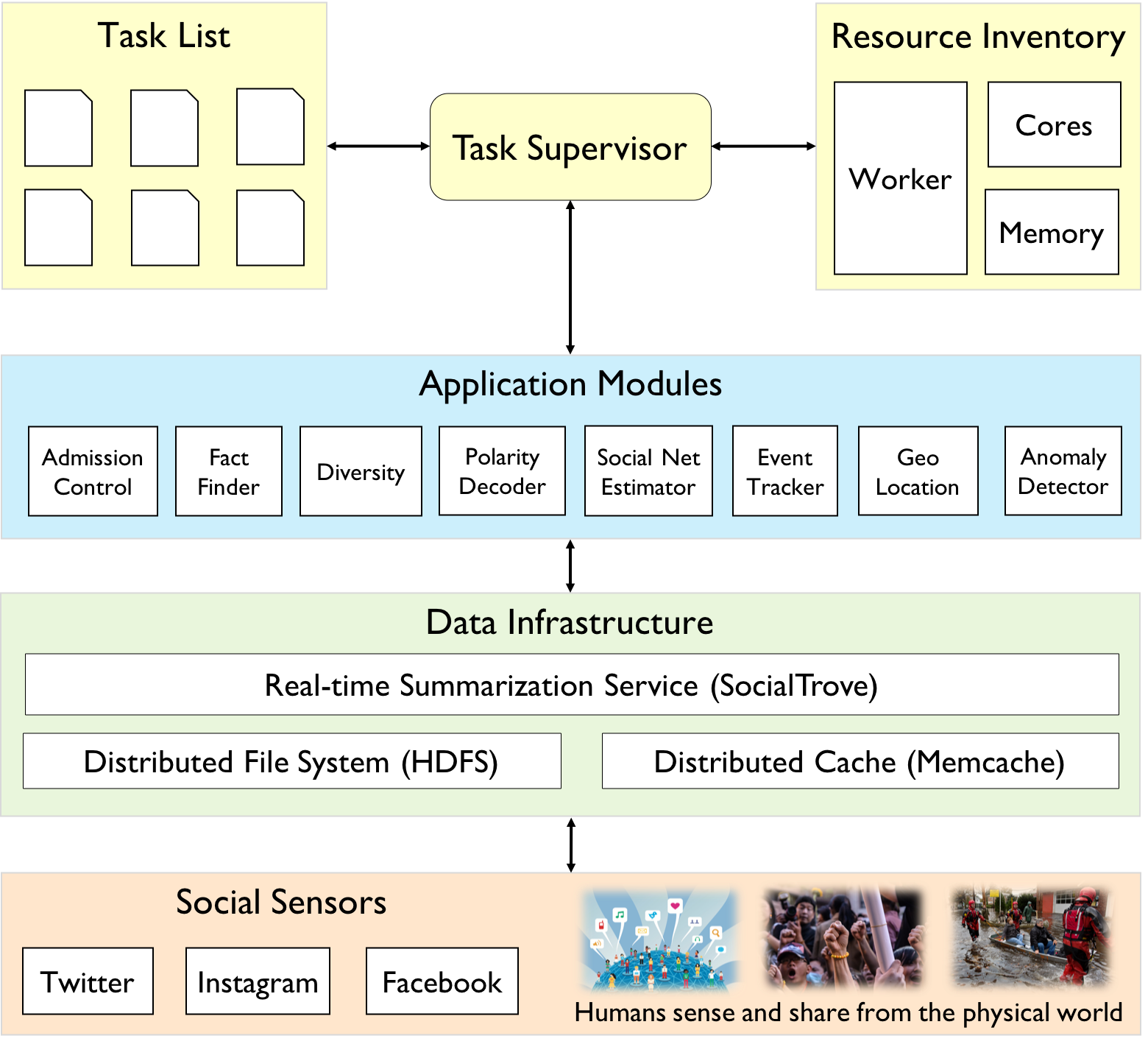 Funded by U.S. Army Research Laboratory,
in collaboration wtih 16 other universities and industry research organizations
under Network Science Collaborative Technology Alliance (NS CTA),
Apollo is a novel social sensing platform for tracking current events
and distilling high value content from large amounts of
noisy social media content. Apollo has a codebase of around 50K
lines of code, and I lead a team of more than 10 graduate student
researchers working on it.
Apollo has been mentioned in the National Academies Press
as an example of cross-genre research, and seleced as a
Golden Nugget of ARL Network Science Collaborative Technology Alliance.
Funded by U.S. Army Research Laboratory,
in collaboration wtih 16 other universities and industry research organizations
under Network Science Collaborative Technology Alliance (NS CTA),
Apollo is a novel social sensing platform for tracking current events
and distilling high value content from large amounts of
noisy social media content. Apollo has a codebase of around 50K
lines of code, and I lead a team of more than 10 graduate student
researchers working on it.
Apollo has been mentioned in the National Academies Press
as an example of cross-genre research, and seleced as a
Golden Nugget of ARL Network Science Collaborative Technology Alliance.
-
- Polarity Meter
-
Funded by U.S. Army Research Laboratory, Polarity Meter
uncovers possible bias and polarity groups from microblog entries related to conflict,
dispute, or situations involving multiple parties with contrasting interest.
This work introduces and validates a model for polarized information network,
proposes algorithms to separate groups, and integrates in a fact-finder
paradigm to improve quality of information.
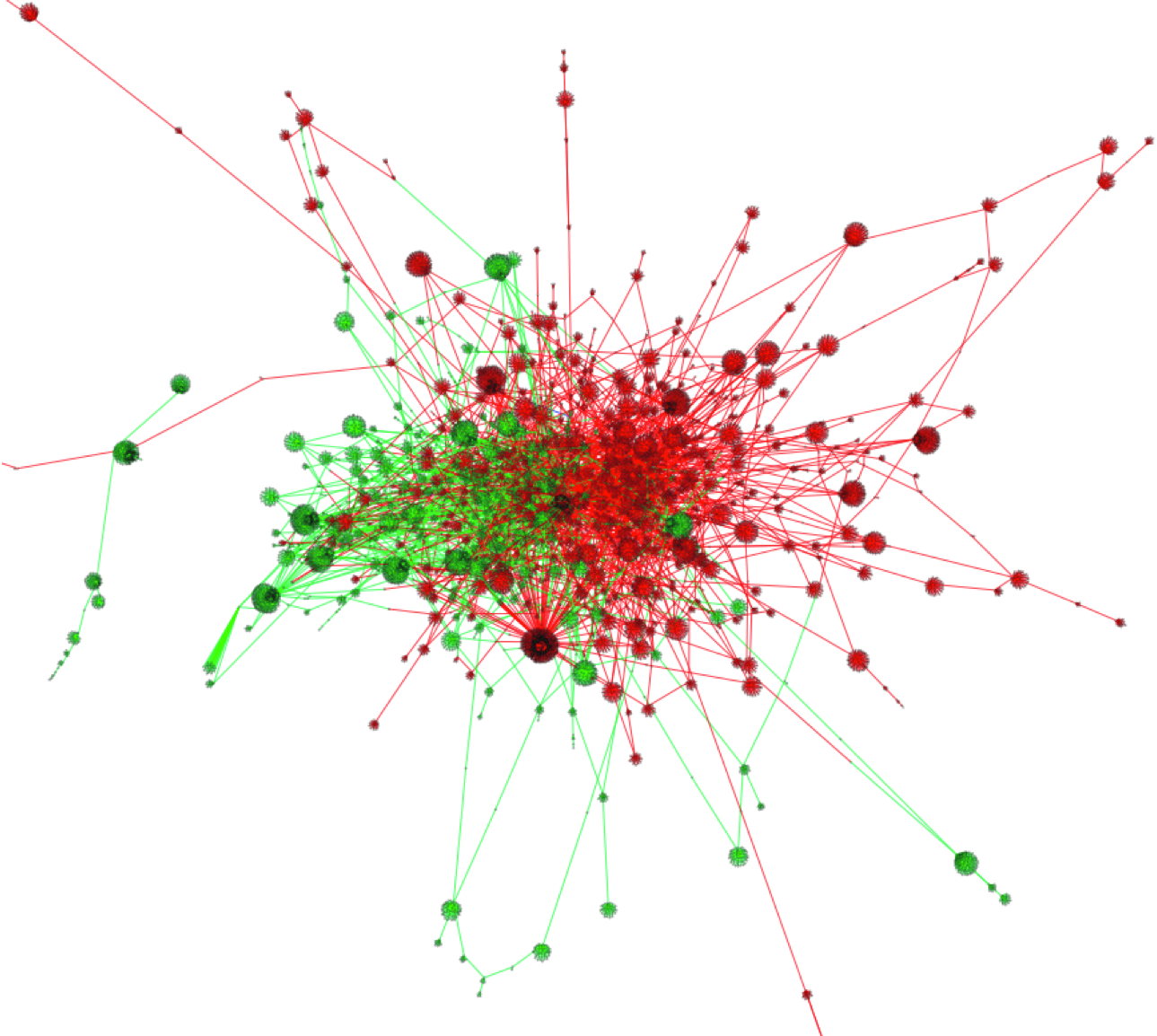
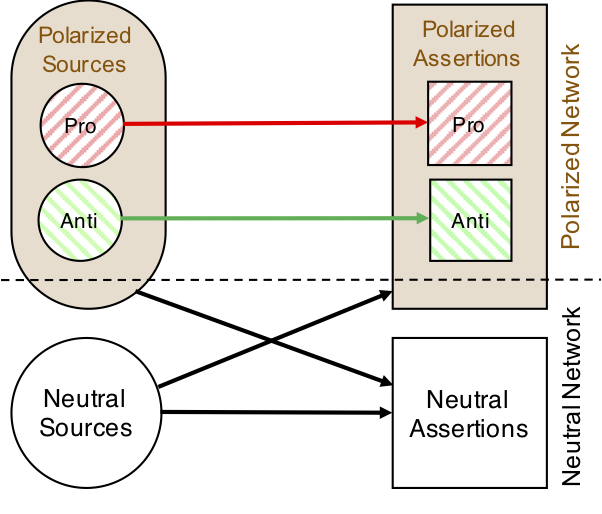
Collaborative research with Charu Aggarwal (IBM Research),
Lance Kaplan (ARL), Boleslaw Szymanski (RPI),
and resulted in peer-reviewed conference publications in INFOCOM 2017, DCoSS 2014, and SPIE 2014.
-
- Humans as Sensors
-
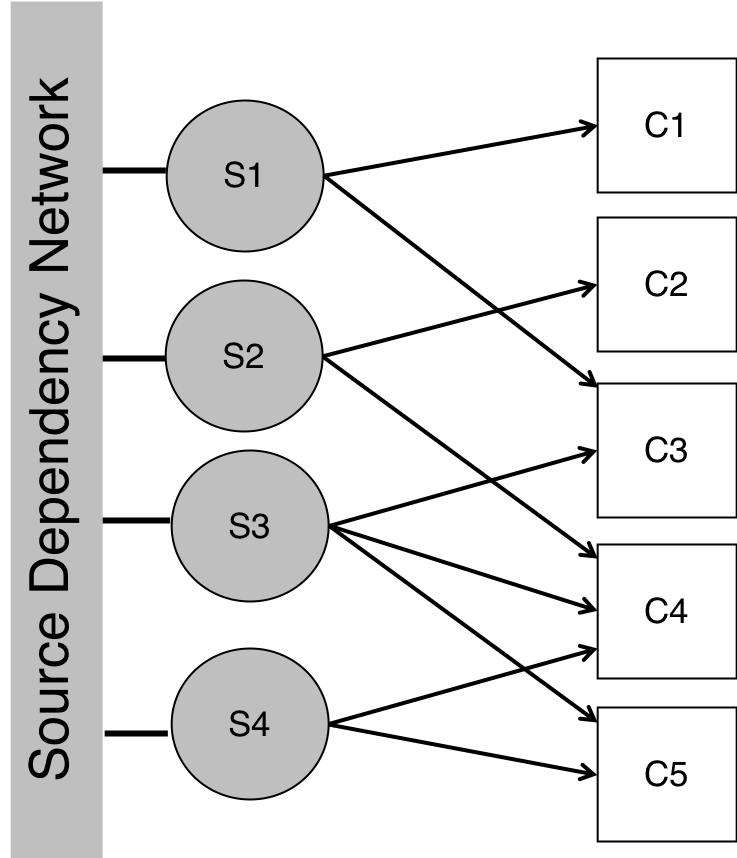 Funded by U.S. Army Research Laboratory,
considers the latent influence network among people, and introduces a
maximum likelihood framework to find reliable information
from unreliable human sources.
We developed batch and streaming algorithms to derive information credibility
from large amount of socially sensed microblog entries.
Collaborative research with
Dong Wang (Notre Dame), Lance Kaplan (ARL), Jiawei Han (UIUC),
Sibel Adali (RPI), Aylin Yener (PSU), and
resulted in a peer-reviewed journal publication in J-STSP 2014,
and many peer-reviewed conference publications in
IPSN 2014, IPSN 2015, IPSN 2016,
FUSION 2014, INSS 2012.
Funded by U.S. Army Research Laboratory,
considers the latent influence network among people, and introduces a
maximum likelihood framework to find reliable information
from unreliable human sources.
We developed batch and streaming algorithms to derive information credibility
from large amount of socially sensed microblog entries.
Collaborative research with
Dong Wang (Notre Dame), Lance Kaplan (ARL), Jiawei Han (UIUC),
Sibel Adali (RPI), Aylin Yener (PSU), and
resulted in a peer-reviewed journal publication in J-STSP 2014,
and many peer-reviewed conference publications in
IPSN 2014, IPSN 2015, IPSN 2016,
FUSION 2014, INSS 2012.
-
- InfoMax
-
Funded by NSF in collaboration with 10 other
universities under Named Data Networking (NDN) project, InfoMax
is a transport-layer data dissemination protocol,
using the recently proposed NDN stack that makes networks aware of
hierarchical data names, as opposed to IP addresses.
Assuming that named objects with longer prefixes are semantically more similar,
InfoMax has the property of minimizing semantic redundancy among delivered data items,
hence offering the best coverage of the requested topic with the fewest bytes.
Resulted in a peer-reviewed conference paper in ICCCN 2015.
-
- eNav: Energy Efficient Vehicular Navigation
-
eNav is a smartphone-based energy-efficient vehicular navigation system. Using the phone's on-board sensors (accelerometer, gyroscope, etc) eNav provides low-power reliable real-time road navigation services, minimizes the need for GPS localization, and results in significant battery savings. Collaborative reseach with Suman Nath (Microsoft Research),
resulted in a Best Poster in IPSN 2014,
and a peer-reviewed conference paper in UbiComp 2015.
-
- Event Threads
-
Funded by U.S. Army Research Laboratory, Event Threads
is a event detection, localization, and tracking library that demonstrates
the utility of exploiting signal processing techniques to reconstruct aspects of
the state of the physical world from social network feeds.
Resulted in a peer-reviewed conference paper in SPIE 2016,
and a book-chapter in Elsevier.
-
- Anomaly Detector
-
Funded by U.S. Army Research Laboratory, Anomaly Detector
fuses social signals with physical sensors to detect and explain anomalous
events in the physical world based on social network feeds.
Resulted in a peer-reviewed conference paper in IQ2S 2014 and a peer-reviewed
journal paper in Elsevier PMC 2016.
-
- PhotoNet+
-
This project develops a new prioritization technique to
addresses the problem of collection
and delivery of a representative subset of pictures, in participatory camera networks,
to maximize coverage when a significant portion of the pictures may be
redundant or irrelevant.
The contribution of this project lies in a new prioritization technique (and its in-network
implementation) that minimizes redundancy among delivered pictures, while also reducing outliers. PhotoNet+ is a collaborative research with Yusuf Sarwar Uddin, and resulted in peer-reviewed demonstration abstract in IPSN 2012.
-
- Speeding Up the Web
-
User engagement in consumer Internet today mostly deals with web applications. These
applications typically result in a traffic pattern consisting of mostly short flows, flows that have less than
400 packets to send. As the latest Internet applications like Software as a Service, Computing as a
Service, and others become more and more ubiquitous, total Internet traffic will be more skewed
towards short flows. But, congestion control algorithms like TCP and XCP are particularly not suited to
short flows, and RCP has still room for improvement in this domain. In this project, we have at first
done an analysis of the flow completion time under ideal processor sharing model. Our findings
suggest that the best way to improve the performance of the tiny flows that have very small number of
packets to send is either improving the round trip delay or devising some protocol that does not wait
for SYN-ACK and starts sending data immediately. However, we can improve the flows for which data
transmission time is comparable to the RTT. Based on our findings, we have proposed a prioritized
congestion control scheme that particularly improves user experience in the Internet by prioritizing
these specific type of short flows. We have simulated our protocol using ns-2 using both core-router
and edge-router traffic models. Simulation results show faster completion time for short flows and
improved total completion times for all flows, confirming the effectiveness of this idea. Collaborative project with Prof. Brighten Godfrey.


 Funded by U.S. Army Research Laboratory,
in collaboration wtih 16 other universities and industry research organizations
under Network Science Collaborative Technology Alliance (NS CTA),
Apollo is a novel social sensing platform for tracking current events
and distilling high value content from large amounts of
noisy social media content. Apollo has a codebase of around 50K
lines of code, and I lead a team of more than 10 graduate student
researchers working on it.
Apollo has been mentioned in the National Academies Press
as an example of cross-genre research, and seleced as a
Golden Nugget of ARL Network Science Collaborative Technology Alliance.
Funded by U.S. Army Research Laboratory,
in collaboration wtih 16 other universities and industry research organizations
under Network Science Collaborative Technology Alliance (NS CTA),
Apollo is a novel social sensing platform for tracking current events
and distilling high value content from large amounts of
noisy social media content. Apollo has a codebase of around 50K
lines of code, and I lead a team of more than 10 graduate student
researchers working on it.
Apollo has been mentioned in the National Academies Press
as an example of cross-genre research, and seleced as a
Golden Nugget of ARL Network Science Collaborative Technology Alliance.


 Funded by U.S. Army Research Laboratory,
considers the latent influence network among people, and introduces a
maximum likelihood framework to find reliable information
from unreliable human sources.
We developed batch and streaming algorithms to derive information credibility
from large amount of socially sensed microblog entries.
Collaborative research with
Dong Wang (Notre Dame), Lance Kaplan (ARL), Jiawei Han (UIUC),
Sibel Adali (RPI), Aylin Yener (PSU), and
resulted in a peer-reviewed journal publication in J-STSP 2014,
and many peer-reviewed conference publications in
IPSN 2014, IPSN 2015, IPSN 2016,
FUSION 2014, INSS 2012.
Funded by U.S. Army Research Laboratory,
considers the latent influence network among people, and introduces a
maximum likelihood framework to find reliable information
from unreliable human sources.
We developed batch and streaming algorithms to derive information credibility
from large amount of socially sensed microblog entries.
Collaborative research with
Dong Wang (Notre Dame), Lance Kaplan (ARL), Jiawei Han (UIUC),
Sibel Adali (RPI), Aylin Yener (PSU), and
resulted in a peer-reviewed journal publication in J-STSP 2014,
and many peer-reviewed conference publications in
IPSN 2014, IPSN 2015, IPSN 2016,
FUSION 2014, INSS 2012.